Executive Summary
In January 2025, Unit 42 researchers identified a series of attacks distributing DarkCloud Stealer. The latest attack chain incorporated AutoIt to evade detection and used a file-sharing server to host the malware. This article explores the chain of events from these recent campaigns and analyzes the characteristics of these attacks.
DarkCloud employs multi-stage payloads and obfuscated AutoIt scripting, making its detection challenging with traditional signature-based methods. Its ability to extract sensitive data and establish command and control (C2) communications highlights the importance of thorough detection and assessment.
Palo Alto Networks customers are better protected from DarkCloud Stealer through our Network Security solutions and Cortex line of products including Advanced WildFire, Cortex XDR and Cortex XSIAM.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Infostealers, AutoIt |
History of DarkCloud Stealer
The threat author has advertised DarkCloud Stealer in hacking forums as early as January 2023. Our telemetry reveals that attackers distributing DarkCloud Stealer have targeted various sectors but have notably focused on government organizations.
A February 2025 report from a Polish telecommunications provider notes that DarkCloud Stealer has appeared in attacks against machines in Poland. Initially spotted in 2022, this information stealer is designed to capture sensitive browser data like credit card information, login credentials and other personal data.
The malware is predominantly distributed through email phishing campaigns and is currently undergoing active development.
Activity Timeline
We have been monitoring this malware family since its appearance in 2022, and we have observed multiple samples that we believe are new variants of DarkCloud Stealer in late January 2025. Figure 1 shows a timeline displaying the sample count of the newly observed DarkCloud variant in January and February of 2025.
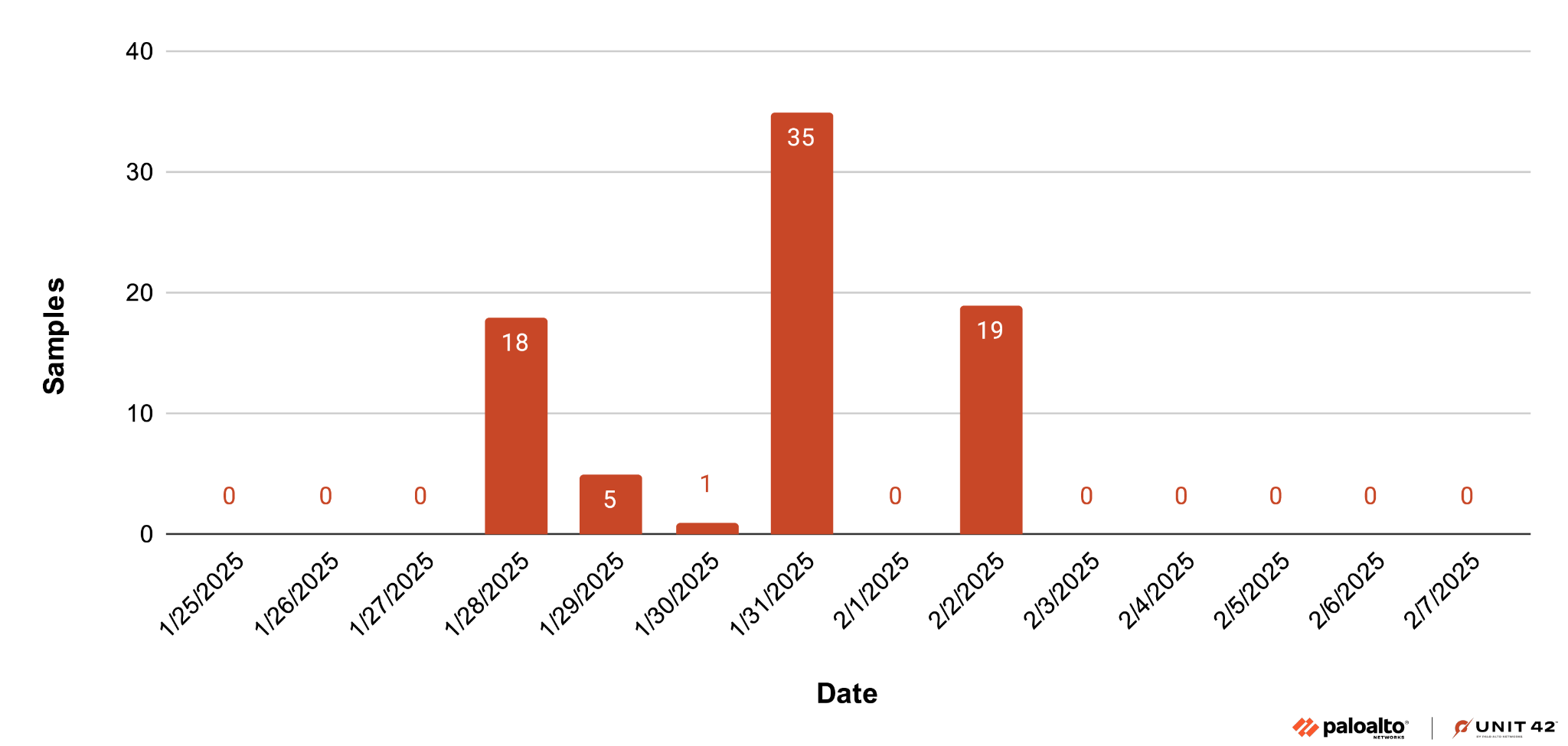
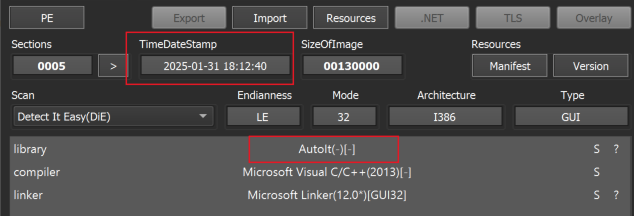
Figure 2 shows one of the samples, an AutoIt-compiled Portable Executable (PE) file in an analysis tool. Figure 3 shows the same sample in another analysis tool. Both tools confirm this sample is an AutoIt compiled PE file.

Delivery Mechanism and Updated Infection Chain
We have observed many different attack chains that vary slightly. Since the variations in the attack chains are minor, we are illustrating just two possible attack chains for this article.
This attack chain starts with a phishing email. As shown in Figure 4, the email might contain a RAR archive or a phishing PDF that eventually downloads the RAR archive.
The RAR archive contains an executable file that eventually delivers the malicious payload. The multi-step nature of this attack underscores its intricacy and stealth. The stages of this attack are:
- A phishing email containing either a RAR archive or a phishing PDF
- In the case of an email with a phishing PDF, the PDF contains a pop-up message asking the victim to download a malicious archive disguised as a software update (from a file-sharing service URL).
- The RAR archive contains an AutoIt compiled PE (EXE) file.
- In addition to the AutoIt script (AU3 file), the AutoIt compiled EXE is packaged with two encrypted data files. One of the files is an encrypted shellcode, and the other file is the XORed payload.
- The AutoIt script builds and runs the final DarkCloud Stealer payload from the two data files.

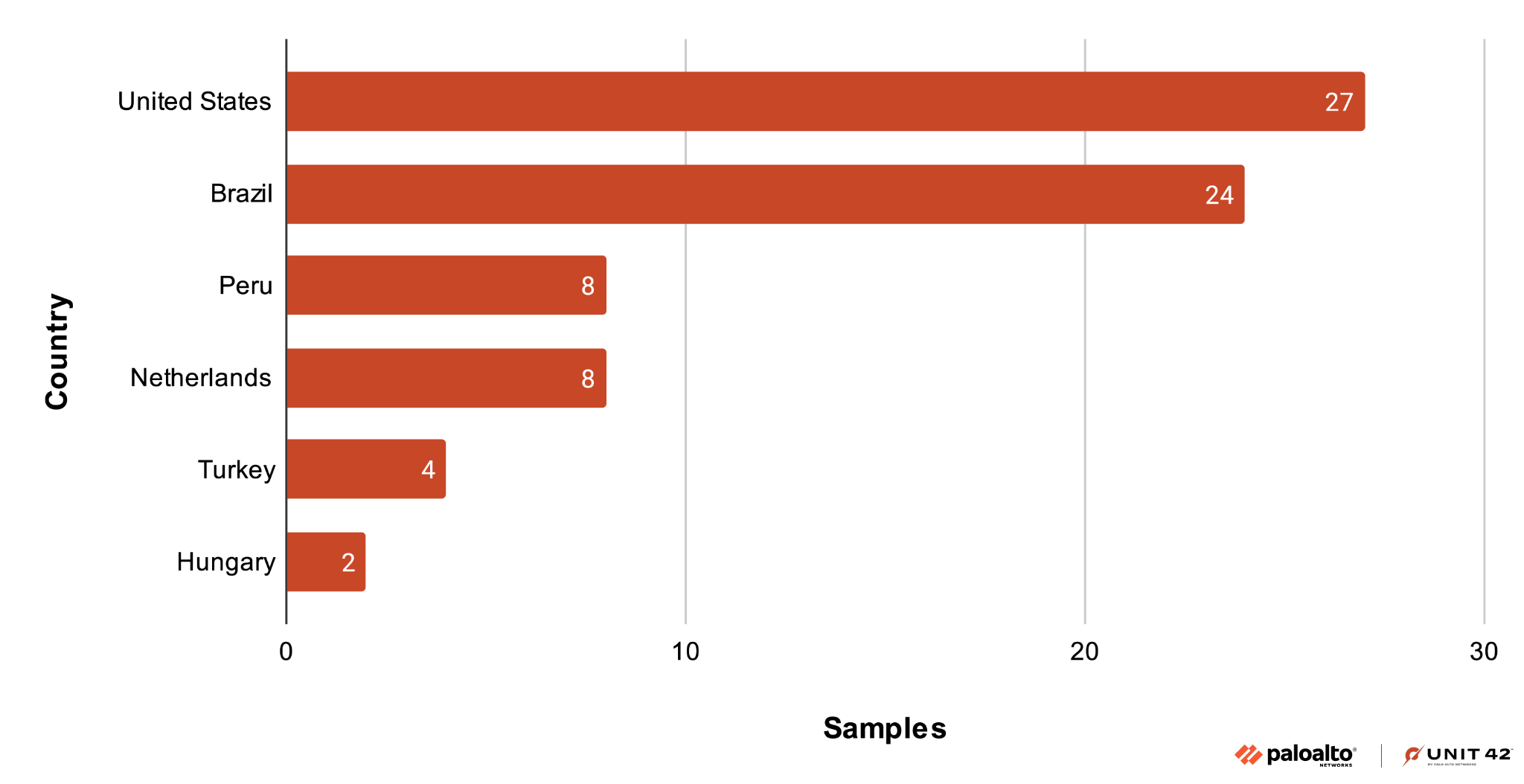
Figure 5 displays the number of these new AutoIt-based DarkCloud samples observed in various affected industries, while Figure 6 shows the geolocation of the samples we have seen.

Technical Analysis
This section delves into the attack chain in these recent DarkCloud Stealer campaigns.
Phishing Email to File-Sharing Service
The initial phishing email contains a PDF file that displays a pop-up message stating the victim's Adobe Flash Player is out of date, as shown below in Figure 7. If a victim clicks the “Download Flash” button, this downloads a RAR archive from a file-sharing service. The archive contains the malicious AutoIt compiled executable.

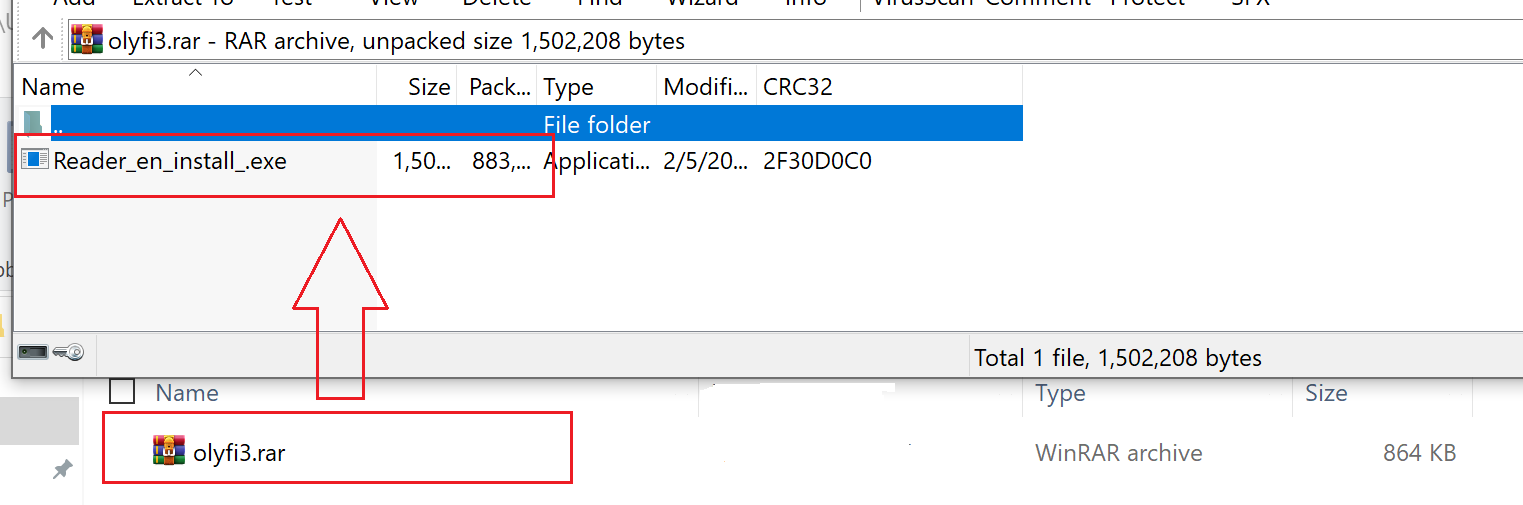
Below, Figure 8 shows the downloaded RAR file and extracted EXE file.
File-sharing services are commonly abused for malware distribution because they offer a convenient way for cybercriminals to host their malicious files. Most of these services can host files that do not require any login credentials or thorough validation of user activities, making them a useful tool in an attack chain.
Another benefit for attackers using file-sharing services is that they can host and remove files for a defined period of time. If someone deletes a file from the server, the attack will eventually cease. But this is also a disadvantage, as the attackers do not have full control compared to owning their own servers. If someone deletes their file-sharing account, the attack chain breaks.
In our case, the malicious RAR file is hosted on the URL hxxps[:]//files.catbox[.]moe/olyfi3.001.
Dropper - AutoIt Compiled Executable
A notable enhancement in this new variant is the incorporation of AutoIt compiled PE files as the dropper component.
AutoIt is a legitimate scripting language for automating the Windows GUI and general scripting tasks. Over the years, criminals have abused it to hide malicious activity. We have published various articles on criminal groups abusing the AutoIt platform.
An AutoIt-compiled executable is typically composed of two parts:
- A standalone AutoIt interpreter
- The compiled script bytecode stored as a resource within the PE file
The compression and encryption prevent easy decompilation of the bytecode. The compiled AutoIt binary handles the decompression of the bytecode before interpreting and executing it.
To better understand how this decompression works, we can analyze the AutoIt script extracted from the AutoIt-compiled PE file. At the beginning of the AutoIt script, as illustrated in Figure 9, the Call(), StringLen() and StringMid() function pointers are assigned to obscurely named global variables using the Execute() function. The string-related global variables serve as the building blocks for a string decoding function used for additional obfuscation.
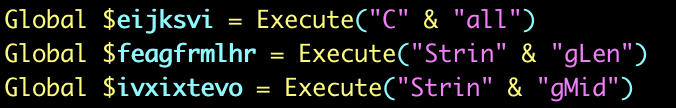
Figure 10 shows the subsequent string decoding function.
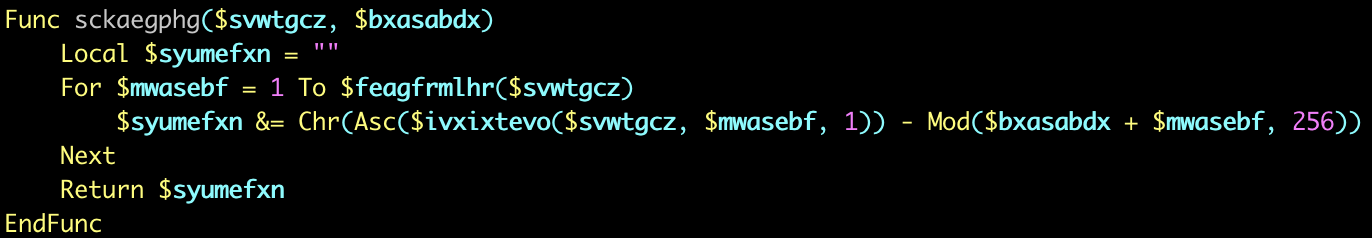
Figure 11 shows the deobfuscated version of the same function from Figure 10.

After implementing the string decoding function, the malware author uses the function to define additional variables, as illustrated in Figure 12. These additional variables use more random names, serving as basic function executions that will be used later.

Figure 13 displays the deobfuscated version of the same code from Figure 12. These definitions closely resemble the initial function executions presented at the start of the script, albeit with an added layer of string obfuscation.

The AutoIt compiled EXE does not simply run the AU3 script alone. The EXE is compiled with two additional files, likely via the native AutoIt FileInstall() function. Specifically, in this sample, the filenames are iodization and plainstones.
Upon closer examination, we see plainstones is an XOR-encrypted PE file. Iodization appears to contain a shellcode pattern. This pattern consists of a series of characters representing hex values, interspersed with a static 8-digit numeric string.
Figure 14 displays a snapshot of the iodization file with the shellcode representation. Upon careful reading, the concatenated values form 0x558bec, which corresponds to the prologue of a subroutine.

Indeed, we can locate the shellcode builder AutoIt script snippet as depicted in Figure 15.

Additionally, the deobfuscated version of this code is shown in Figure 16.

Our analysis led to the following three insights.
- In some samples of this malware, the associated global variable linking to the execution of StringLower() is not defined. This could potentially be a bug in the malware authors' toolchain.
- The extractShellCode() function shown above in Figure 16 includes case sensitivity as an optional parameter, although it is not used in this case. This suggests the existence of potential variants with higher levels of obfuscation that use upper and lower case letters to encrypt the binary data file.
- The same extractShellCode() function also includes the capability of bitwise AND assignment (&=) for encryption that is not used in this context. Once again, this indicates the possibility of variants with additional obfuscation methods applied to encrypt the binary data file.
The AutoIt script first creates a DllStructure to host the shellcode. It then calls VirtualProtect() to change the memory protection to PAGE_EXECUTE_READWRITE. Finally, the script executes the shellcode using CallWindowProc().
Figure 17 displays the deobfuscated code showing these functions. Notably, the entry point of the shellcode is not at the beginning of the injected blob but at the 9168th byte (or 0x23D0 in hex), as indicated by the parameters of CallWindowProc.

Upon examining the entry point of the shellcode, as depicted in Figure 18, we observed that soon after the 558BEC prologue, the code promptly initiates the construction of a string in memory. This string serves as the XOR decryption key for the previously mentioned plainstones file.

Figure 19 displays the decrypted output as a PE file. Subsequently, the shellcode builds this PE file in memory and eventually executes it.

Payload - DarkCloud Executable
This section shows various functionalities employed by the final DarkCloud payload. First, as shown in Figure 20 below, we can identify the final payload executable as DarkCloud Stealer because of the DARKCLOUD signature string found in the sample.

In general, DarkCloud Stealer is a comprehensive data-stealing malware that collects and exfiltrates information such as:
- Computer names
- Usernames
- Screenshots
- Contacts
- Browser passwords
- Email client passwords
This infostealing functionality is shown in Figure 21 below.

Stealing Browser and Mail Client Data
The payload attempts to retrieve saved usernames and passwords from various Chrome-based and Gecko-based browsers. Figure 22 shows a list of folders that the DarkCloud sample iterates through to scan for files such as logins.json, key4.db and signons.sqlite.

Figure 23 shows that the malware then checks each profile from the mail client and gathers saved credentials and data. Once it collects all the data, the malware consolidates it into a single file that it can exfiltrate from the victim's machine to the C2 server.

This sample checks for user accounts and credit card details from various Chromium-based and Gecko-based browsers. It searches for information from various types of popular credit cards, as shown in Figure 24 below.
Credit Card Information Stealing

SMTP and FTP Credential Stealing
This sample attempts to retrieve saved login credentials from various FTP client applications and decrypts them for exfiltration as shown in Figure 25.

Anti-Analysis and Other Crucial Functionalities
DarkCloud incorporates numerous anti-analysis techniques, including checks for analysis tools such as:
- WinDbg
- Fiddler
- TCPView
- Process Explorer
- VMWare Tools
- Wireshark
- Process Monitor
The sample uses typical junk code and fake API calls to make analysis more difficult. This sample also checks for the victim’s public IP address using the web services below to obtain geolocation.
- hxxp://showip[.]net
- hxxp://www[.]mediacollege[.]com/internet/utilities/show-ip.shtml
Lastly, persistence is achieved through an addition to the RunOnce registry key:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\
Conclusion
DarkCloud Stealer has been active since 2022 and is continuously evolving. Attackers often modify their techniques for delivering malware, making detection and prevention more difficult. Palo Alto Networks monitors these campaigns, using a range of static and dynamic techniques to detect and prevent them.
Stealers of this type are well-known elements of the threat landscape, and there are many approaches to protecting customers from these evolving attacks. These methods include dynamic and behavioral detections, as well as more reactive signature or pattern-based solutions.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.001 | Phishing |
| Execution | T1204 | User Execution
Scheduled Task/Job |
| Persistence | T1053 | Scheduled Task/Job |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Credential Access | T1555 | Credentials from Password Stores
Steal Web Session Cookie Unsecured Credentials Steal Application Access Token |
| Discovery | T1087 | Account Discovery
Software Discovery Process Discovery System Service Discovery |
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of the IoCs shared in this research.
- Cortex XDR and XSIAM are designed to:
- Prevent the execution of known malicious malware, and also prevent the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
SHA256 hash for the malicious PDF file:
- bf3b43f5e4398ac810f005200519e096349b2237587d920d3c9b83525bb6bafc
SHA256 hash for the downloaded RAR archive:
- 9940de30f3930cf0d0e9e9c8769148594240d11242fcd6c9dd9e9f572f68ac01
SHA256 hash of AutoIt-compiled EXE for DarkCloud Stealer:
- 30738450f69c3de74971368192a4a647e4ed9c658f076459e42683b110baf371
- 1269c968258999930b573682699fe72de72d96401e3beb314ae91baf0e0e49e8
URL hosting malicious RAR archive:
- hxxps[:]//files.catbox[.]moe/olyfi3.001
Additional Resources
- Decoding the Inner Workings of DarkCloud Stealer – Cyble Blog
- Dark Cloud – a new stealer on the Polish network – CERT Orange Poland











 Get updates from Unit 42
Get updates from Unit 42